DRM allow authors of a digital file to make sure that any future users of said file is limited in their use of it.
It is done with encryption. The producer encrypts the file, which means that the file becomes unreadable to anyone that doesn't have an "encryption key", which is, in layman's terms, a very long password. The producer does not give the encryption key to the user (buyer usually). Instead, he integrates the key in a program that he produces as well, and that the user has to use to open the file.
Since the file produced can only be opened by a program under the control of the same producer, the producer can decide what the user will be allowed to do with the file, and what he shouldn't be allowed to do.
DRM adopts a proactive strategy to secure content by limiting access to it as well as the number of things that can be done to the content (e.g copying, downloading, etc.). There are various ways to deal with DRM and new techniques emerge every day. Numerous DRM systems work through encryption or with code inserted in the computerized content to restrict access or use. These systems can control the occasions, gadgets, individuals, or time spans that the content can get to or be introduced.
Advantages of having a DRM tool
a) Content Protection/ Encryption
The most common protection given by DRM is through encryption and digital watermarking.
Encryption
Encryption is the process of scrambling information embedded within a digital object so that it cannot be used without a password or a unique key. This could include encoding the terms and conditions for which the material can be used. The use of the work is allowed only when the conditions of the key can be met.
Watermarking
Digital watermarking embeds the information into data. Watermarks can either be visible or invisible. It helps to reduce the likelihood that someone will bypass it or try to make illegal copies.
b) Access Control
Access control (AC) is the act of controlling access to resources at its most basic level. AC often is used as a ‘what and when’ model of security—that is what/who has access and to when/what can they access?
Software and Computer GamesSoftware and computer games have implemented various forms of DRM throughout recent decades. Many forms of its modern implementation have been intrusive and frustrating for many users legitimate and otherwise. One of the most common methods is through the use of serial keys. The content can only be accessed if a legitimate serial key is provided by the user normally in the form of an alphanumeric string
c) Access Tracking
Who, what, when all the information about file access can be tracked in recent DRM tools. You can restrict the number of downloads, have a time limit for file access. Access Tracking is one of the major security ask of clients looking for DRM tools.
Let's move on and list out some of the top DRM tool providers right now
Digify is document security and virtual data room software that's easy to use and takes only minutes to set up. Thousands of companies save time using Digify in sharing confidential documents with partners, clients, and investors. It is easy to use and gives control of who can see what and who has seen what. It is very easy for recipients of attachments to view them as they do not require special software. If you have different sets of users, Digify helps you manage access permission at varying degrees. You can restrict forwarding, revoke access, or make your files private or public. You can also set rules for downloading, so you can decide which users can save locally or print a confidential document.
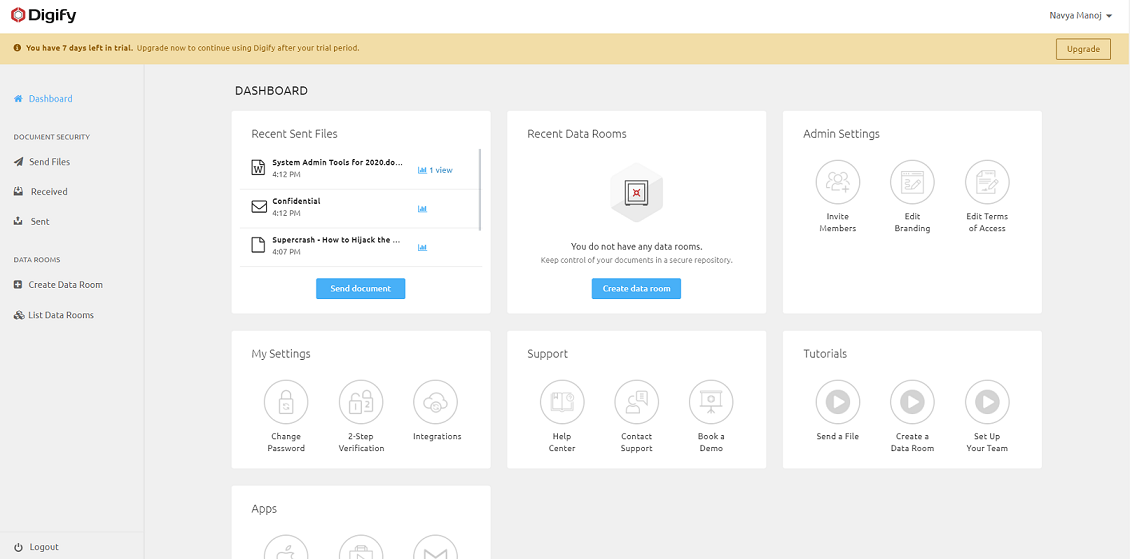
Pros -
- The ability to send documents to multiple people in a way that does not allow for them to save the documents or forward the documents (thus helps to prevent plagiarism).
- Excellent solution to keep document secure while sharing and communicating inside & outside of your organization - no matter how large or small.
- can encrypt files and deny access after a certain date. There are a lot of permission options and that works well.
Cons -
- It is Expensive.
- The permissions setting process is a bit cumbersome and adding new users & getting permissions correct could be easier.
FileCloud DRM protects important, sensitive business documents against intellectual property theft, piracy, and leakage. This security travels with your files wherever they go, protecting them with AES-certified 256-bit encryption at all times. You'll be able to instantly revoke any recipient's access to data, at any time, from the FileCloud Portal and protect your documents, files, and e-books against unauthorized copying and distribution. FileCloud DRM stops unauthorized sharing, taking screenshots, copying, the printing of your intellectual property (contracts, sales/marketing reports, eBooks, training materials, and other sensitive documents). The sender can instantly restrict or revoke access any time after sending and also set maximum access counts.
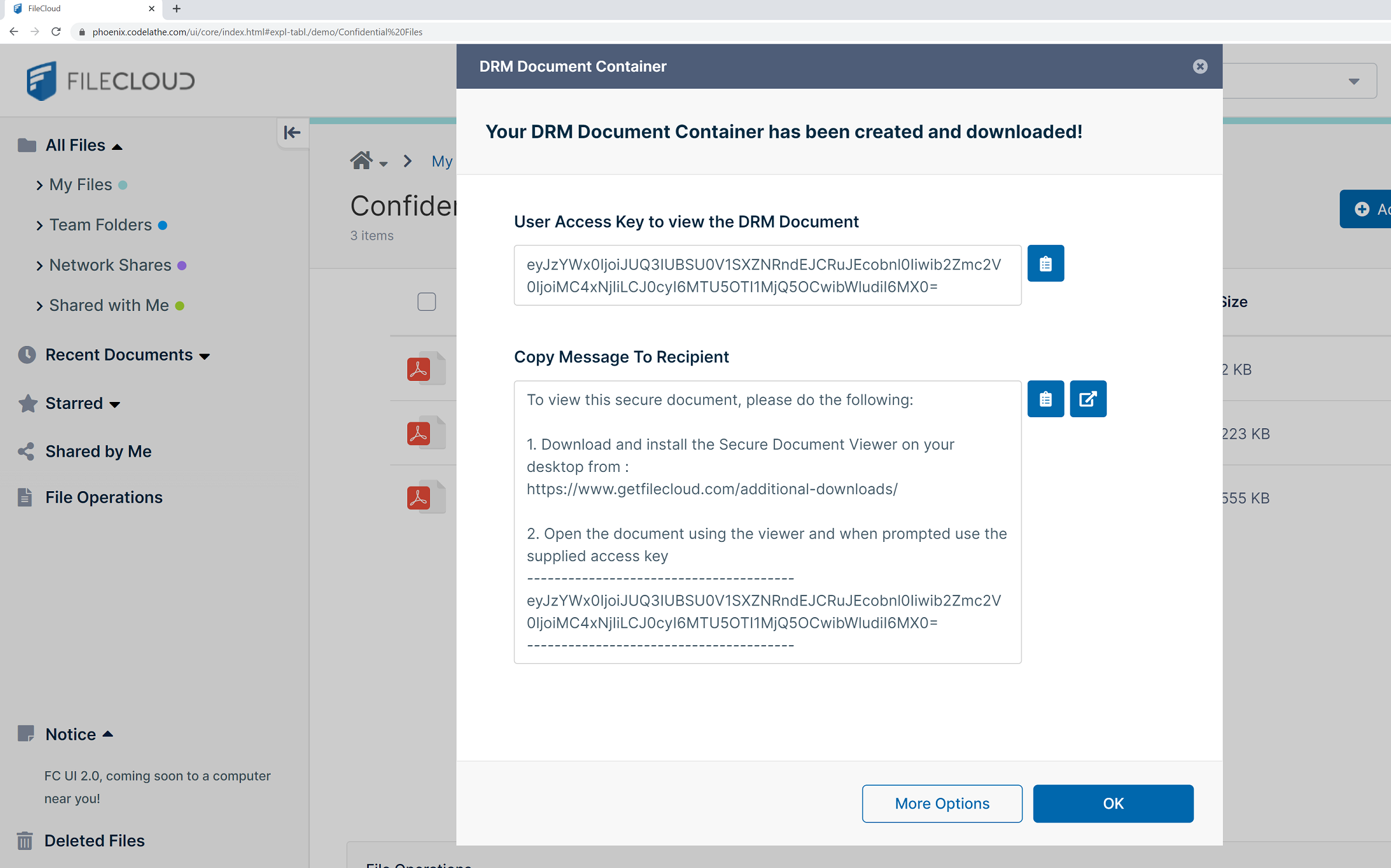
Pros-
- Cost-effective DRM solution in the market.
- FileCloud DRM lets you securely export multiple documents in an encrypted document container (AES 256 encryption) and share it via email or FileCloud.
- FileCloud DRM Container supports multiple file formats. That includes Microsoft Office (Word, Powerpoint), PDF and image (jpeg, png) files.
Cons-
- Do not yet have gmail or outlook integration.
- Relatively new DRM tool but with strong File sharing features
Locklizard Safeguard PDF Security provides total PDF DRM protection and control over your documents through a multi-layered protection mechanism that does not rely on passwords. Locklizard Safeguard PDF Security enforces DRM controls, uses US Government strength encryption (AES 256-bit), real-time licensing, and public-key technology. There are no passwords, plug-ins, or dependencies on other applications to compromise your security, or complex PKI structures to manage.


Pros-
- A good range of DRM controls
- Unobtrusive to users
- Easy to implement
- Good and responsive technical support.
- Locklizard has two types of DRM copy protection software for documents, files, ebooks, etc. which are-Safeguard PDF Security, and Enterprise PDF DRM.
- It has a dynamic document watermarking feature, providing additional PDF protection so that even if photocopies are made of printed copies of your PDF, or users take photographs of the screen, your Intellectual Property remains secure.
- It allows you to lock user access to country locations i.e. allow or disallow specific country access. You can also lock user access to specific IP addresses or a range of IPs (for instance, you can lock document use to the IP addresses of your office computers to ensure that they can only be viewed from the office).
Cons -
- It does not support forms.
- It is expensive.
- It could do with a bit more auditing features.
Vitrium Security is mainly used to protect, control, and analyze the accessibility of the content. It comprises of features that take care of the whole operation. From securely sharing the content to keeping track of the file, online video integration, etc the system manages it all. The content security solution comes in two editions: Professional and Enterprise. The Professional Edition includes all core content protection features from permission control to distribution security. On the other hand, the Enterprise Edition includes all functionalities in the previous edition plus automation, single sign-on (SSO), integration, and more.
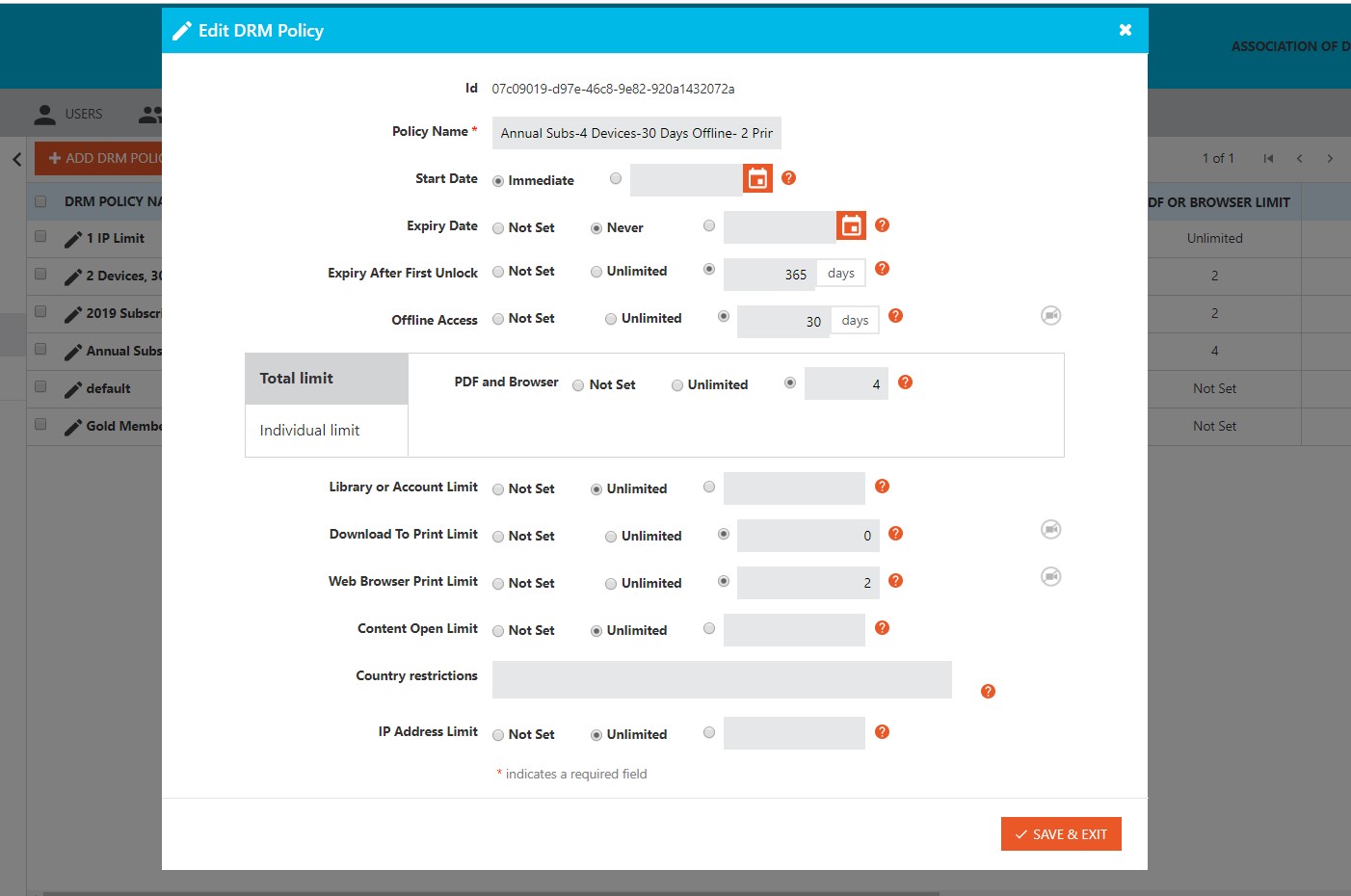
Pros -
- There are many different levels you can set from expiry time to watermarking.
- It also has an easy to use interface for clients/users. The control dashboard is simple, neat, and clean.
- The online web viewer is an easy way for customers to view the report. It also enables viewing on tablet computers.
- The team at Vitrium has created a great product and provides outstanding customer service.
Cons-
CapLinked is an intuitive, easy-to-use, and superior virtual data room solution that enables enterprise and external collaborators to work together on secure online workspaces, share data, files, and documents with each other, and concentrate more on closing deals. DRM features include manage and control how external collaborators are viewing, accessing, editing, and printing the documents and files they stored within the platform. This is to ensure that any sensitive and confidential information contained in those documents and files won’t fall into the wrong hands. Watermarking features are also included as users share documents and files.
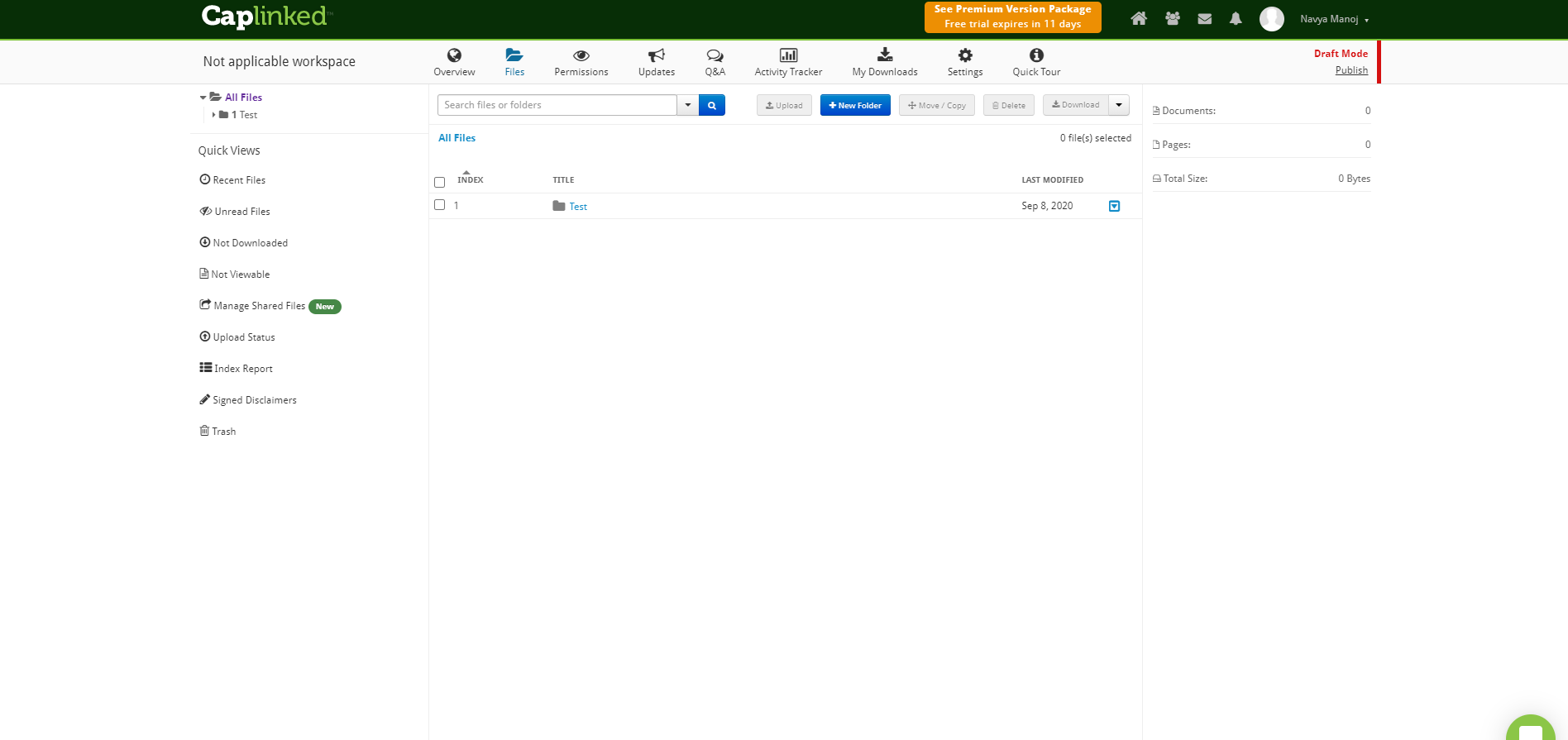
Pros-
- Robust features, such as activity tracker, security, Q&A, and customized messages. - Everything is recorded by Caplinked.
- The CapLinked platform is super easy to navigate and share and lets you keep confidential documents secure at all times. It allows different levels of control for each group which saves a lot of time.
- Reasonably priced, secure, and easy to use the software. Great customer support!
Cons-
- It lacks export tools and better data trends. Offers no easy way to archive old data into the new system.
- Could use more flexibility on the use of graphics, custom reporting, and dashboard.
- Setting file permissions is a bit clunky, as is assigning user permissions and inviting users.
DocSend delivers a powerful, comprehensive analytics tool that focuses on documents and how people interact with it. Whenever you send a sales material such as an online catalog or a sales copy of your newest product, you often wonder what actions your recipients took upon receiving your documents. Or whether they open your documents at all.DocSend provides you with tools that grant you absolute control over your documents even after you send them. You can set up control features such as passwords, download permissions, and even update your documents from time to time if there is a typo.

Pros-
- Integration with Gmail.
- Awareness of when your audience engages with time-sensitive documents.
- It's easier to share files with the team and work while on the go because of this platform. It doesn’t matter whether you are using Google Mail or Outlook Express because you could sync it without experiencing any issues at all.
FileOpen RightsManager is a client/server solution for encrypting and managing access to documents from your desktop. With RightsManager, you encrypt your documents locally, so there is no need to upload unencrypted documents to an unknown server. You maintain complete control of your source files at all times.RightsManager offers a free trial. With regards to system requirements, RightsManager is available as SaaS, and Windows software. Costs start at $3000.00/year. RightsManager includes online support and business hours support.

Pros-
- Implement programming functions with programmers relatively easily.
- Good customer support.
- The FileOpen software operates in three environments: installed on the desktop, via browser plug-ins, and via native HTML. Each of these has a different functional profile.
Cons-
- Troubleshooting is sometimes difficult.
- Not all features are available in all modes.
- The system is a bit clunky.
MagicBox is an award-winning, next-generation K-12 education publishing and distribution platform that offers key customization services. MagicBox allows K-12 and higher-education publishers to create, manage, and distribute digital content through custom web and mobile apps. It provides features such as easy integration of interactive multimedia elements, standard and video assessments, compliance with industry standards, and detailed analytics. Plus, it offers robust digital rights management services, allowing greater control over who can access the digital content. So, if you are looking for the best virtual classroom solution, MagicBox is the platform you need.

Pros-
- Features like expiry control, sales control, and content control.
- Analytics- Get detailed reports of content consumption patterns and usage trends
- Compliance with industry standards like QTI, LTI, SCORM, and TinCan.
Cons-
- It is expensive
- Their key target is educational institutions and their features reflect that.
- No access control and file-sharing options.
The truth is, your employees may find USB sticks, external hard drives, webmail, and smart devices more convenient than traditional organizational tools when it comes to transferring files. Unfortunately, this creates a gap in control and visibility for IT departments, exposing companies to compliance and security risks. As a result, organizations are slowly shying away from consumer-grade secure document sharing to more secure options.

By Team FileCloud