Out of numerous Windows admin tools, PowerShell is one of the most valuable tools. It offers scripting language flexibility and command line speed, making it incredibly effective to automate important security chores. Using PowerShell, Windows administrators gain the ability to automate various tasks, like managing users, deploying patches, and rotating logs. Using PowerShell isn’t difficult, once you get the hang of it. In fact, you can use it for both security-based jobs and certain Windows administration tasks. Do you want to monitor attack activities or need to manage your certificates? PowerShell has you covered.
Due to the versatility of PowerShell, it’s not unusual for someone to create a PowerShell module or script that focuses on security. Windows admins enjoy access to a wide range of scripts from the community, capable of handling security tasks of varying magnitudes. This covers everything from network forensics to penetration testing, certificate management to event logging. Below we’ll take a look at how the endless potential of PowerShell security scripts proves indispensable to Windows admins, and discuss the 10 best ones among them.
1. List $Profile
The actual user connected to the machine is dubbed “user.” On the other hand, “host” is used for the host application that connects to the PowerShell engine. Thus, a single host can have different profiles, and each one of them has an associated file stored in a specific location. For easy maintenance and security, a single file can be used for managing multiple profiles. All the user needs to do is add conditions to this file to prevent a non-supported command from being executed by the “host.” There are lots of people who’d be more comfortable separating the profiles into individual files. This would free them from the burden of having to maintain a PS1 that is extremely complex.
2. Add-PSSnapIn
Windows PowerShell security script allows for the creation of custom profiles. These profiles support snap-ins and modules. Though this slows down the start-up time of the PowerShell console, it bodes well for the security of your system.
PowerShell profiles assist with system administration, but being just a PS1 file, it remains exposed to the risk of malicious code. Even when the default location is in a user’s directory and the file remains protected from access by all users, it can be changed to execute commands without your knowledge. To prevent this from happening, you can do two things – either you can make use of NTFS permissions to set limits on modifying permissions for these files, especially for the admin account or you can sign the file digitally and then configure PowerShell in a way that it employs a more restrictive strategy for execution. The recent PowerShell versions add an extra layer of security by helping users set up their choice of strategic security.
3. Get-ExecutionPolicy
Suppose you are working on a server that is entirely unknown to you. In this case, you first need to know what sort of execution policy is currently being used before you try to run some script. Finding out this information is easy when you use the command Get-ExecutionPolicy.
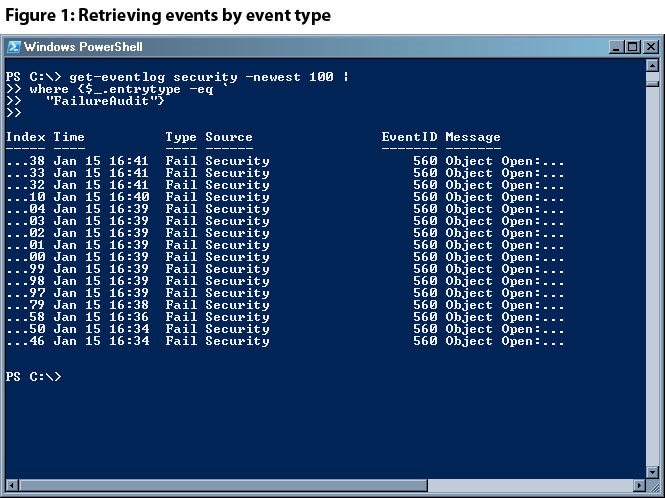
4. Get-EventLog
http://windowsitpro.com/site-files/windowsitpro.com/files/archive/windowsitpro.com/content/content/99879/figure1.jpg
PowerShell may actually be used to parse the event logs present in your system. Though there are several ways to go about this process, the best one for this particular command is just to offer the –Log switch accompanied by the log file name. For example, you can use commands like Get–EventLog –Log “Application” to view the Application log. You then need to filter the output and understand whether your system is safe or not.
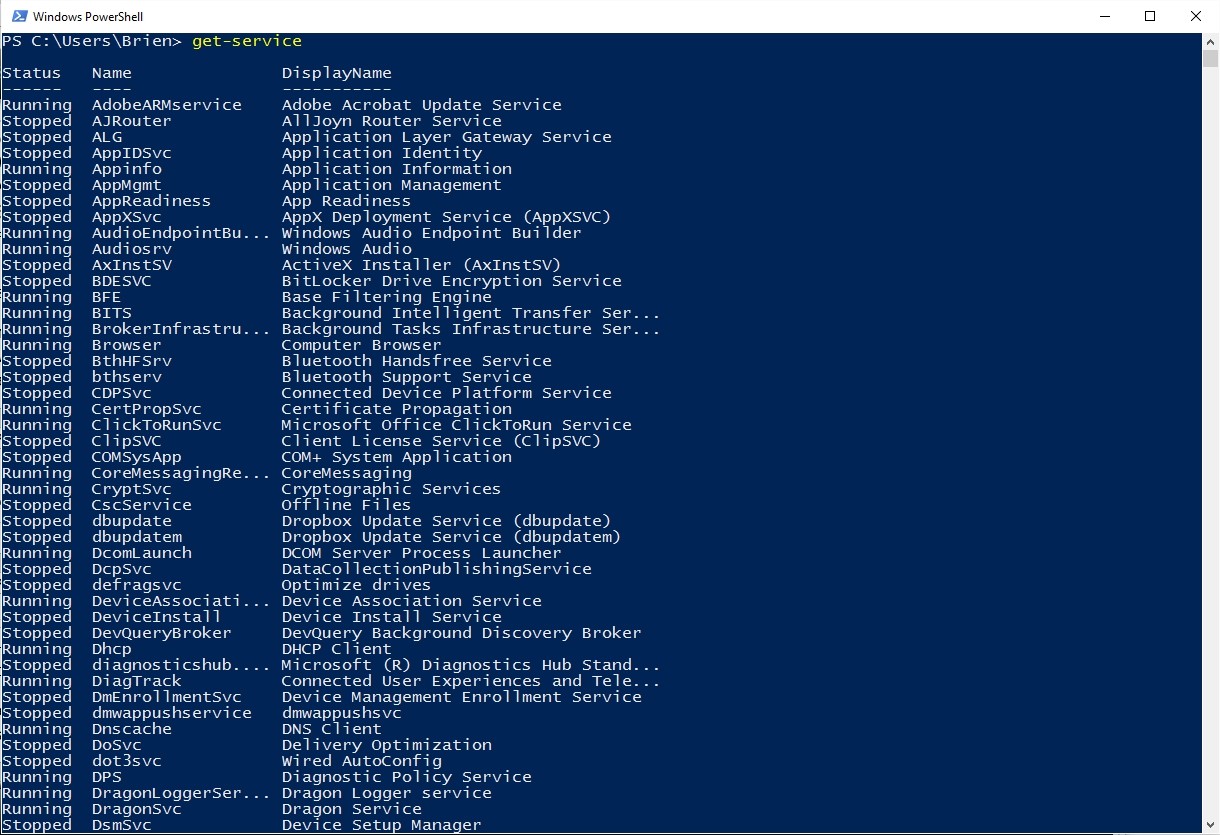
5. Get-Service
https://redmondmag.com/articles/2016/01/22/~/media/ECG/redmondmag/Images/2016/01/ForEachService_Fig1.ashx
When you give this command, it offers up a list of every service that is currently installed on your system. If you think that a particular service is worth checking out for security, then it’s possible to append the “–Name” switch as well as the service name. You’re allowed to use wildcards. Once you’re done, you’ll be shown the state of the service by Windows.
6. Get-Process
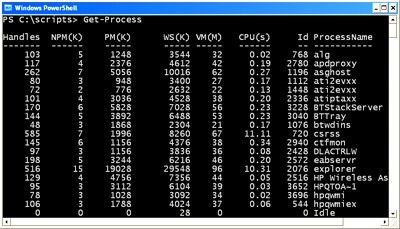
Unlike the Get-Service command in PowerShell, which displays a list of the different system services at your discretion, Get-Process command, if used capably, can display a whole list of each and every process that the system currently runs.
7. Stop-Process
It is not uncommon for a particular process to lag or freeze up from time to time. This is often a nuisance and causes a lot of problems. To prevent this, use the Get-Process command so that you have the process ID or name of the program that didn’t respond. You can then terminate this problematic process using the Stop-Process command. A process can be terminated based on its process ID or name. However, you should understand that the process ID changes from one session to another.
8. Digital Signature
The TimeStampServer command helps you verify whether a particular PowerShell script was signed at a certain time. The majority of certificates remain valid for a period of one year. Once the date of expiration comes closer, the usage of this parameter doesn’t allow the code itself to expire. You are then able to use it as long as it hasn’t been modified. If a modification has been conducted, then you’ll have to sign it again using a valid certificate.
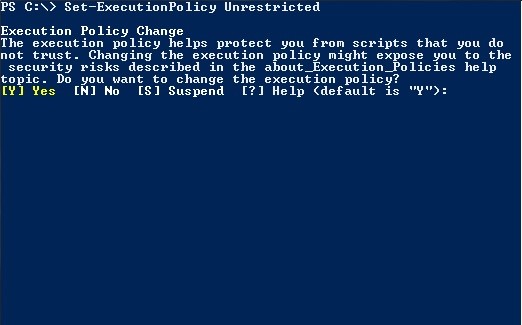
9. Set-Execution Policy
http://2.bp.blogspot.com/-DvqcAZzw_RM/T3GzmL_CRXI/AAAAAAAAAG4/b89yOhFrUIg/s1600/2.jpg
You are capable of creating and executing PowerShell scripts as you want. However, Microsoft no longer supports scripting by default. This has been done to prevent any malicious code from getting executed in a PowerShell setting. This command can then be used to control the security level of the PowerShell scripts. There are four different layers of security, ranging from Unrestricted to Restricted, Remote Signed to All Signed. This kind of flexibility is much-need in a PowerShell security script, and you can set them with the help of the Set-Execution Policy command along with the policy name.
10. Set-AuthenticodeSignature
While trying to configure a group policy object, you must sign your profile with this particular certificate. Otherwise, the security of your Windows system will be seriously undermined.
In a PowerShell environment, it is extremely important for Windows admins to secure their system via scripts, but you shouldn’t let that turn into a restriction. Thus, prior to deploying your policy, you must have a test plan in place that will ensure no problem from the signed scripts. The PowerShell security scripts listed above are indispensable since they’ll keep the system well-protected and efficient.
Author: Rahul Sharma
Source:
http://www.infoworld.com/article/3148664/security/10-essential-powershell-security-scripts-for-windows-administrators.html
https://www.simple-talk.com/sysadmin/powershell/powershell-day-to-day-sysadmin-tasks-securing-scripts/
https://technet.microsoft.com/en-us/library/ee176961.aspx

By Team FileCloud